Describe the Use of Digital Certificates in Encryption
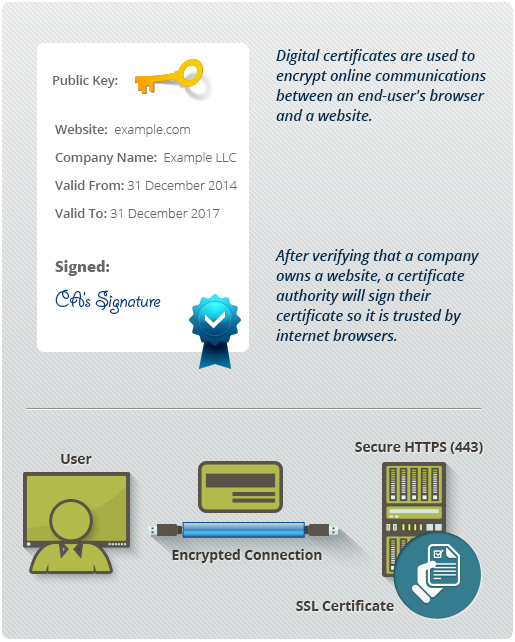
Something like a drivers license a passport a company ID or a school ID. A Digital Certificate is used to encrypt online datainformation communications between an end-users browser and a website.
What Is A Digital Certificate Definition Of Digital Ssl Certificates
After verifying that a company owns a website the certificate authority will sign their certificate so it is trusted by internet browsers.
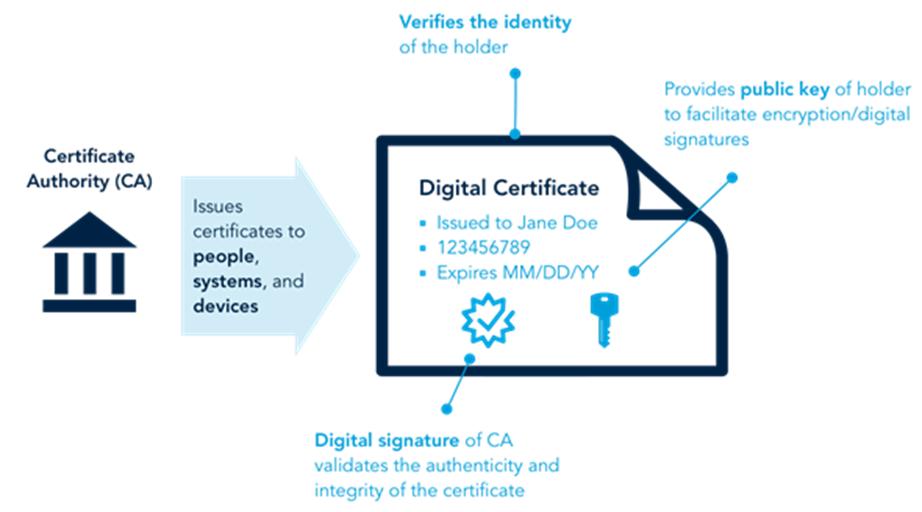
. Digital certificates make it possible for digital signatures to be used as a way to authenticate digital information. Why Email Security Certificates Are Vital to Secure Email Communication. Throughout this module you learn about the different elements of cryptography and their application in cybsecurity.
Digital certificate authentication helps organizations ensure that only trusted devices and users can connect to their networks. Certificate algorithms The Elliptic Curve Cryptographic ECC and RSA algorithms are the public key algorithms that are supported by DCM from which you can choose to generate the public. While digital certificates play a vital security role they also present security risks.
Certificate algorithms are cryptographic algorithms that describe the mathematical procedures that are used for creating key pairs and performing digital signature operations. If not lets take a moment to break it down. If you know how an SSLTLS certificate works then you already know how an encryption certificate work.
Digital Signature Followed by Encryption. Cryptography is foundational to protecting the confidentiality integrity and availability of information. As this form is less secured this is not preferable in the industry.
A digital certificate is issued by a certification authority CA. Digital Certificate - Is a notice that guarantees a suer or a website is legitimate. Cert will help that user confirm.
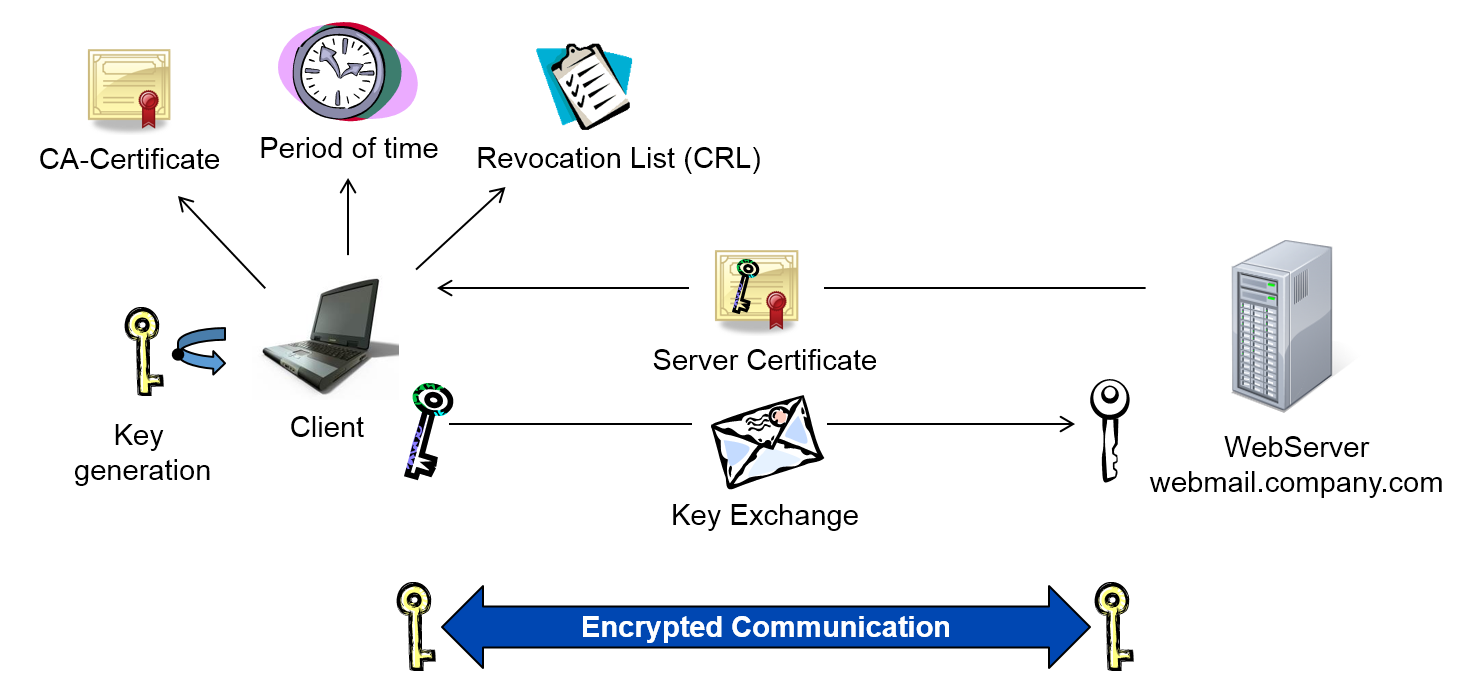
Digital signatures often are used to ensure that an imposter is not participating in an Internet transaction. However the fact that the region decryption key is stored on the hardware level in the DVD players substantially weakens this form of protection. A certificate management system is a good way to mitigate many of those risks.
Describe the role of encryption and digital certificates in a public key infrastructure. Digital certificates are used with self-signatures and message encryption. Describe concepts of cryptography.
A digital certificate primarily acts like an identification card. The certificate purpose defines the intended primary use of the certificate. Theyre used to create the encrypted channel thats used for client communications.
A certificate with this purpose will contain cryptographic keys for signing data only. It basically tells other people who you are. Another common use of digital certificates is to confirm the authenticity of a.
How an Encryption Certificate Works. Email encryption certificate is the digital certificate used to sign the email to ensure the receiver that the email has come from a legitimate person and also that the email has not. We use digital certificates for all range of things everything from web servers to IoT devices.
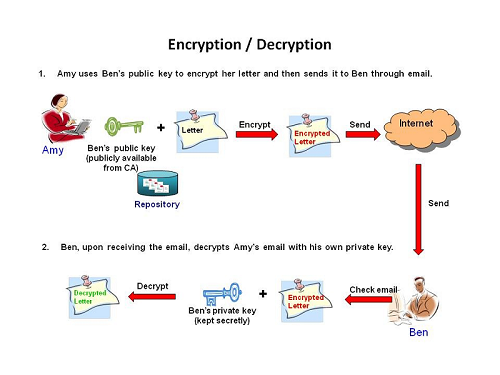
A digital certificate is necessary for a digital signature because it provides the public key that can be used to validate the private key that is associated with a digital signature. Digital certificates are electronic files that work like an online password to verify the identity of a user or a computer. Digital certificates are for sharing public keys to be used for encryption and authentication.
Digital certificates will establish the identity of the sender and provide the receiver with the means to encode a reply. Secure Site - A website that uses encryption techniques to secure its data. A certificate with this purpose will contain cryptographic keys for encryption and decryption.
Encryption and digital certificates protect electronic transactions by authentication process. Encryption of digital signatures can be carried out in two major forms. Its a digital file that contains information that.
The certificate purpose can be one of four settings. The best example of practical use of certificate-based encryption is Content Scrambling System CSS which is used to encode DVD movies in such a way as to make them playable only in a part of the world where they are sold. An SSLTLS certificate is just one part of the data encryption process that works based on public key infrastructure PKI and public key encryption.
2 Objectives Describe the role encryption plays in a firewall architecture Explain how digital certificates work and why they are important security tools Analyze the workings of SSL PGP and other popular encryption schemes Discuss Internet Protocol Security IPSec and identify its protocols and modes. A digital certificate also known as a public key certificate is used to cryptographically link ownership of a public key with the entity that owns it. In this method the sender signature is exploited by the receiver and the information is shared with the external party without encryption.
For the sake of this discussion lets stick to SSLTLS and how they work in that context. Digital certificates overview. A digital certificate authenticates the Web credentials of the sender and lets the recipient of an encrypted message know that the data is from a trusted source or a sender who claims to be one.
Digital certificates include the public key being certified identifying information about the entity. A digital certificate is a file or electronic password that proves the authenticity of a device server or user through the use of cryptography and the public key infrastructure PKI. E-commerce application comonly use digital certificates.
And defending against cyberattacks. When a browser arrives at the website it receives a copy of the SSL certificate thats installed on that server for the respective site and performs a series of checks to ensure that the certificate is.

Digital Certificates And Pki Identification For Development
Ogcio Digital Certificates For Electronic Transactions Uses Of Digital Certificates
Comments
Post a Comment